Threats
Table of contents
- Threat Modeling
- Threats
- Weak or stolen credentials
- Insecure authentication protocols
- Insufficient access controls
- Improper privilege escalation
- Data leakage or unauthorized access
- Insecure data storage
- Inadequate network segmentation
- Man-in-the-Middle attacks
- Resource exhaustion
- Distributed DoS (DDoS) attacks
- Misconfigured security settings
- Insecure default configurations
- Delayed patching of software
- Lack of vulnerability scanning
- Malicious or negligent insiders
- Unauthorized data access or theft
- Unauthorized physical access
- Theft or destruction of hardware
- Vulnerabilities in third-party components
- Lack of oversight on third-party activities
- Threat detection
- Indicators of compromises
Threat Modeling
Threat modeling is a process that helps identify and prioritize potential security threats to a system or application. The goal of threat modeling is to identify security risks early in the development process and proactively mitigate them, rather than waiting for vulnerabilities to be discovered after deployment.
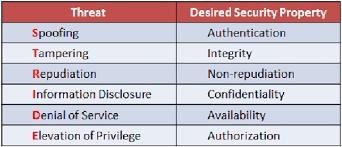
One popular method for conducting threat modeling is called STRIDE, which stands for Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege. These are the six types of security threats that can affect a system, and by considering each of them in turn, a threat model can help identify potential vulnerabilities and attacks.
The STRIDE methodology is often used in combination with a diagram designer tool, such as Microsoft’s Threat Modeling Tool or the open-source OWASP Threat Dragon. These tools allow you to create a visual representation of the system or application you are analyzing, and to map out potential threats and attack vectors.
Explains the six types of security threats in the STRIDE methodology:
| STRIDE Threat | Description |
|---|---|
Spoofing | Impersonating a user, device, or system in order to gain unauthorized access or perform malicious actions. Examples include phishing attacks or using a fake SSL certificate to intercept data. |
Tampering | Modifying data or code in transit or at rest, in order to introduce errors, gain unauthorized access, or perform other malicious actions. Examples include modifying the source code of an application or altering data in a database. |
Repudiation | Denying or disavowing actions or events, in order to evade accountability or responsibility. Examples include denying that an action was taken, or that data was accessed. |
Information Disclosure | Revealing confidential or sensitive information to unauthorized parties, whether intentionally or accidentally. Examples include disclosing passwords or user data, or exposing private keys. |
Denial of Service | Disrupting or degrading the availability or functionality of a system or application, through network attacks, resource exhaustion, or other means. Examples include Distributed Denial of Service (DDoS) attacks or flooding a server with requests. |
Elevation of Privilege | Gaining additional access or privileges beyond those that were initially granted, in order to perform unauthorized actions or escalate an attack. Examples include exploiting a software vulnerability to gain administrative access or using a social engineering technique to obtain sensitive information. |
Implementation
Step 1: Define the Scope
Identify the application or system within the DevSecOps pipeline that you want to perform threat modeling for. For example, let’s consider a microservices-based application deployed using containerization and managed by Kubernetes.
Step 2: Gather Information
Gather information about the application’s architecture, design, and deployment. This includes understanding the components, their interactions, data flows, and external dependencies.
Step 3: Identify Threats and Assets
Identify the critical assets and sensitive data involved in the application. Consider both internal and external threats that could compromise the security of these assets. For example: Unauthorized access to customer data stored in a database Injection attacks on APIs or containers Misconfiguration of Kubernetes resources leading to unauthorized access or privilege escalation
Step 4: Assess Vulnerabilities and Risks
Evaluate the architecture and design to identify potential vulnerabilities and risks associated with the identified threats. Consider the security implications at each stage of the DevSecOps pipeline, including development, testing, deployment, and operations. For example: Insecure container images containing known vulnerabilities Lack of proper access controls on Kubernetes resources Weak or outdated authentication mechanisms
Step 5: Prioritize and Mitigate Risks
Prioritize the risks based on their potential impact and likelihood of occurrence. Develop mitigation strategies and recommendations to address each identified risk. Consider integrating security controls and best practices into the DevSecOps pipeline. For example: Implementing automated vulnerability scanning and patch management for container images Applying secure configuration practices for Kubernetes resources Enforcing strong authentication and access controls at all stages of the pipeline
Step 6: Continuously Monitor and Improve
Incorporate threat modeling as an iterative process within the DevSecOps lifecycle. Regularly review and update the threat model as the application evolves or new risks emerge. Continuously monitor the system for potential threats and vulnerabilities.
Real-case Example:
In a DevSecOps context, consider a scenario where a development team is building a cloud-native application using microservices architecture and deploying it on a container platform. The threat modeling process could involve identifying risks such as:
- Insecure container images with vulnerabilities
- Weak authentication and authorization mechanisms
- Inadequate logging and monitoring for containerized applications
- Misconfiguration of cloud resources and access controls
- Insecure communication between microservices
- Injection attacks on API endpoints
Based on the identified risks, mitigation strategies could include:
- Implementing automated vulnerability scanning and image hardening for containers
- Applying strong authentication and authorization mechanisms, such as OAuth or JWT tokens
- Incorporating centralized logging and monitoring solutions for containerized applications
- Establishing proper cloud resource management and access control policies
- Encrypting communication channels between microservices
- Implementing input validation and security controls to prevent injection attacks
Threat Matrix
This matrix provides a starting point for identifying potential threats and corresponding mitigations based on different categories.
| Threat Category | Threat Description | Potential Mitigation |
|---|---|---|
Authentication | Weak or stolen credentials | Implement strong password policies, multi-factor authentication, and password hashing algorithms. |
Authentication | Insecure authentication protocols | Use secure authentication protocols (e.g., TLS) and avoid transmitting credentials in plaintext. |
Authorization | Insufficient access controls | Implement RBAC (Role-Based Access Control) and apply the principle of least privilege. |
Authorization | Improper privilege escalation | Limit privilege escalation capabilities and regularly review user permissions. |
Data Protection | Data leakage or unauthorized access | Encrypt sensitive data at rest and in transit, and implement proper access controls. |
Data Protection | Insecure data storage | Follow secure coding practices for data storage, including encryption and secure key management. |
Network Security | Inadequate network segmentation | Implement proper network segmentation using firewalls or network policies. |
Network Security | Man-in-the-Middle attacks | Use encryption and certificate-based authentication for secure communication. |
Denial-of-Service (DoS) | Resource exhaustion | Implement rate limiting, request validation, and monitoring for abnormal behavior. |
Denial-of-Service (DoS) | Distributed DoS (DDoS) attacks | Employ DDoS mitigation techniques, such as traffic filtering and load balancing. |
System Configuration | Misconfigured security settings | Apply secure configuration guidelines for all system components. |
System Configuration | Insecure default configurations | Change default settings and remove or disable unnecessary services. |
Vulnerability Management | Delayed patching of software | Establish a vulnerability management program with regular patching and updates. |
Vulnerability Management | Lack of vulnerability scanning | Conduct regular vulnerability scans and prioritize remediation. |
Insider Threats | Malicious or negligent insiders | Implement proper access controls, monitoring, and employee training programs. |
Insider Threats | Unauthorized data access or theft | Monitor and log user activities and implement data loss prevention mechanisms. |
Physical Security | Unauthorized physical access | Secure physical access to data centers, server rooms, and hardware components. |
Physical Security | Theft or destruction of hardware | Implement physical security controls, such as locks, surveillance systems, and backups. |
Third-Party Dependencies | Vulnerabilities in third-party components | Perform due diligence on third-party components, apply patches, and monitor security advisories. |
Third-Party Dependencies | Lack of oversight on third-party activities | Establish strong vendor management practices, including audits and security assessments. |
Tools
| Threat Category | Threat Description |
|---|---|
Microsoft Threat Modeling Tool | A free tool from Microsoft that helps in creating threat models for software systems. It provides a structured approach to identify, analyze, and mitigate potential threats. |
OWASP Threat Dragon | An open-source threat modeling tool that enables the creation of threat models using the STRIDE methodology. It provides an intuitive interface and supports collaboration among team members. |
PyTM | An open-source threat modeling tool specifically designed for web applications. It allows the modeling of various aspects of an application’s architecture and helps in identifying potential threats. |
ThreatModeler | A commercial tool that offers a comprehensive platform for threat modeling. It provides a visual modeling interface, automated threat analysis, and integration with other security tools and frameworks. |
IriusRisK | A commercial tool that combines threat modeling with risk management. It supports multiple threat modeling methodologies, provides risk assessment capabilities, and offers integration with other tools and platforms. |
TMT (Threat Modeling Tool) | An open-source command-line tool developed by OWASP for threat modeling. It supports the STRIDE methodology and allows for the automation of threat modeling processes. |
Secure Code Warrior | While not a traditional threat modeling tool, it offers interactive training modules and challenges that can help developers understand and identify potential threats during the development process. |
Threats
Weak or stolen credentials
PyTM
This code creates a threat model using PyTM and represents the “Weak or Stolen Credentials” threat scenario. It includes actors such as “Attacker” and “Insider,” a server representing the application server, and a datastore representing the user’s data.
The threat model defines the “Weak or Stolen Credentials” threat and includes attack paths such as “Password Guessing/Brute Force Attack,” “Credential Theft,” and “Insider Threat.” It also defines the impact of these threats, such as unauthorized access to user data and data breaches.
The code generates a threat model diagram in PNG format, named “weak_or_stolen_credentials_threat_model.png.”
from pytm import TM, Server, Datastore, Actor
# Create a new threat model
tm = TM("Weak or Stolen Credentials Threat Model")
# Create actors
attacker = Actor("Attacker")
insider = Actor("Insider")
# Create server and datastore
server = Server("Application Server")
datastore = Datastore("User Datastore")
# Define weak or stolen credentials threat
tm.add_threat()
tm.threat.name("Weak or Stolen Credentials")
tm.threat.description("Threat of weak or stolen user credentials")
# Define attack paths
tm.attack_path(attacker, server, "Password Guessing/Brute Force Attack")
tm.attack_path(attacker, server, "Credential Theft")
tm.attack_path(insider, server, "Insider Threat")
# Define impact
tm.data_flow(server, datastore, "Unauthorized Access to User Data")
tm.data_flow(server, datastore, "Data Breach and Exposure of Sensitive Information")
# Generate the threat model diagram
tm.generate_diagram("weak_or_stolen_credentials_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Weak or Stolen Credentials:
Concepts:
- Credentials: Usernames and passwords or other authentication tokens used for user authentication.
- Weak Credentials: Easily guessable or commonly used credentials that can be easily exploited.
- Stolen Credentials: Credentials obtained by unauthorized individuals through various means, such as phishing or data breaches.
- Authentication Mechanisms: Methods used to verify user identities and grant access.
- Unauthorized Access: Gaining access to a system or application without proper authorization.
Users:
1. Attackers:
- Threat: Exploitation of Weak or Stolen Credentials
- Attempts to gain unauthorized access to the system by using weak or stolen credentials.
2. System Administrator:
- Threat: Weak Credential Management
- Fails to enforce strong password policies or implements weak authentication mechanisms.
3. User:
- Threat: Credential Theft or Compromise
- Falls victim to phishing attacks or unknowingly uses weak or easily guessable credentials.
Components:
1. Authentication System:
- Manages user authentication and access controls.
- Data Flow: User authentication requests and verification.
2. Credential Storage:
- Stores user credentials securely.
- Data Flow: Storing and retrieving user credentials.
3. User Interface:
- Provides a platform for user interaction and login.
- Data Flow: User input of credentials and authentication responses.
Interactions:
1. Attackers:
- Utilizes brute-force techniques or exploits stolen credentials to gain unauthorized access to the system.
- Attempts to access restricted resources or perform malicious activities.
2. System Administrator:
- Implements weak password policies or authentication mechanisms that can be easily exploited.
- Fails to enforce multi-factor authentication or regular password updates.
3. User:
- Enters credentials during the login process, which are sent to the authentication system for verification.
- May fall victim to phishing attacks, leading to the disclosure of their credentials.
4. Authentication System:
- Verifies user credentials against stored values and grants access based on authentication policies.
- Stores and retrieves user credentials securely.
5. Credential Storage:
- Safely stores user credentials using appropriate encryption and hashing techniques.
- Protects credentials from unauthorized access or disclosure.
Insecure authentication protocols
PyTM
This code creates a threat model using PyTM and represents the “Insecure Authentication Protocols” threat scenario. It includes actors such as “Attacker” and “User,” a server representing the application server, and a datastore representing the user’s data.
The threat model defines the “Insecure Authentication Protocols” threat and includes attack paths such as “Eavesdropping” and “Man-in-the-Middle Attack.” It also defines the impact of these threats, such as unauthorized access to user data and data breaches.
The code generates a threat model diagram in PNG format, named “insecure_authentication_protocols_threat_model.png.”
from pytm import TM, Server, Datastore, Actor
# Create a new threat model
tm = TM("Insecure Authentication Protocols Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create server and datastore
server = Server("Application Server")
datastore = Datastore("User Datastore")
# Define insecure authentication protocols threat
tm.add_threat()
tm.threat.name("Insecure Authentication Protocols")
tm.threat.description("Threat of using insecure authentication protocols")
# Define attack paths
tm.attack_path(attacker, server, "Eavesdropping")
tm.attack_path(attacker, server, "Man-in-the-Middle Attack")
# Define impact
tm.data_flow(server, datastore, "Unauthorized Access to User Data")
tm.data_flow(server, datastore, "Data Breach and Exposure of Sensitive Information")
# Generate the threat model diagram
tm.generate_diagram("insecure_authentication_protocols_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Insecure Authentication Protocols:
Concepts:
- Authentication Protocols: Standards or mechanisms used for verifying user identities during the authentication process.
- Insecure Authentication Protocols: Protocols that are susceptible to security vulnerabilities or can be easily exploited.
- Man-in-the-Middle (MitM) Attacks: Attacks where an attacker intercepts and modifies communication between two parties.
- Unauthorized Access: Gaining access to a system or application without proper authorization.
Users:
1. Attackers:
- Threat: Exploitation of Insecure Authentication Protocols
- Attempts to intercept or manipulate authentication traffic to gain unauthorized access.
2. System Administrator:
- Threat: Configuration of Insecure Authentication Protocols
- Misconfigures authentication protocols or fails to implement secure alternatives.
3. User:
- Threat: Exposure of Credentials
- Communicates with the system using insecure authentication protocols, which can lead to the exposure of credentials.
Components:
1. Authentication System:
- Manages user authentication and access controls.
- Data Flow: User authentication requests and verification.
2. Authentication Protocol:
- Specifies the rules and procedures for authenticating users.
- Data Flow: Exchange of authentication messages between the user and the authentication system.
3. Attacker's System:
- Represents the system used by attackers to intercept or manipulate authentication traffic.
- Data Flow: Interception and modification of authentication messages.
Interactions:
1. Attackers:
- Exploits vulnerabilities in insecure authentication protocols to intercept or modify authentication messages.
- Attempts to obtain user credentials or gain unauthorized access to the system.
2. System Administrator:
- Misconfigures authentication protocols, such as using weak encryption or outdated protocols.
- Fails to implement secure alternatives, such as using strong cryptographic algorithms or multi-factor authentication.
3. User:
- Initiates the authentication process by sending authentication requests to the system.
- Communicates with the system using insecure authentication protocols, which can be intercepted by attackers.
4. Authentication System:
- Verifies user credentials and grants access based on the authentication protocol in use.
- May be vulnerable to attacks if insecure authentication protocols are implemented or misconfigured.
5. Authentication Protocol:
- Facilitates the exchange of authentication messages between the user and the authentication system.
- Can be compromised if it is insecure or susceptible to attacks like Man-in-the-Middle.
Insufficient access controls
PyTM
This code creates a threat model using PyTM and represents the “Insufficient Access Controls” threat scenario. It includes actors such as “Attacker” and “User,” a server representing the application server, and a datastore representing the sensitive data.
The threat model defines the “Insufficient Access Controls” threat and includes attack paths such as “Unauthorized Access” by the attacker and “Privilege Escalation” by the user. It also defines the impact of these threats, such as unauthorized access to sensitive data and data leakage.
The code generates a threat model diagram in PNG format, named “insufficient_access_controls_threat_model.png.”
from pytm import TM, Actor, Server, Datastore
# Create a new threat model
tm = TM("Insufficient Access Controls Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create server and datastore
server = Server("Application Server")
datastore = Datastore("Sensitive Datastore")
# Define insufficient access controls threat
tm.add_threat()
tm.threat.name("Insufficient Access Controls")
tm.threat.description("Threat of insufficient access controls on sensitive data")
# Define attack paths
tm.attack_path(attacker, server, "Unauthorized Access")
tm.attack_path(user, server, "Privilege Escalation")
# Define impact
tm.data_flow(server, datastore, "Unauthorized Access to Sensitive Data")
tm.data_flow(server, datastore, "Data Leakage")
# Generate the threat model diagram
tm.generate_diagram("insufficient_access_controls_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Insufficient Access Controls:
Concepts:
- Access Controls: Mechanisms used to enforce authorized access to resources.
- Insufficient Access Controls: Inadequate or misconfigured access controls that allow unauthorized access to resources.
- Unauthorized Access: Gaining access to a resource without proper authorization.
- Privilege Escalation: Exploiting vulnerabilities to gain higher levels of access privileges.
Users:
1. Attackers:
- Threat: Unauthorized Access or Privilege Escalation
- Attempts to bypass or exploit insufficient access controls to gain unauthorized access to resources or escalate privileges.
2. System Administrator:
- Threat: Misconfiguration of Access Controls
- Misconfigures access control settings, allowing unauthorized access or granting excessive privileges.
3. User:
- Threat: Unauthorized Access to Restricted Resources
- Attempts to access resources they are not authorized to access due to insufficient access controls.
Components:
1. Resource:
- Represents a system or data that needs to be protected.
- Data Flow: Access requests and responses.
2. Access Control Mechanisms:
- Controls access to resources based on defined policies.
- Data Flow: Authorization checks and access grants or denials.
Interactions:
1. Attackers:
- Exploits vulnerabilities or misconfigurations in access control mechanisms to gain unauthorized access.
- May attempt privilege escalation to gain higher levels of access.
2. System Administrator:
- Misconfigures access control settings, such as assigning incorrect permissions or not properly segregating access.
- Fails to regularly review and update access control policies and configurations.
3. User:
- Requests access to resources through the system.
- May attempt to access restricted resources by bypassing or circumventing access controls.
4. Resource:
- Contains sensitive data or functionality that needs to be protected.
- Enforces access control policies to determine whether a user should be granted access.
5. Access Control Mechanisms:
- Enforce access control policies and determine whether a user has sufficient privileges to access a resource.
- May be misconfigured or contain vulnerabilities that can be exploited by attackers.
Improper privilege escalation
PyTM
This code creates a threat model using PyTM and represents the “Improper Privilege Escalation” threat scenario. It includes actors such as “Attacker” and “User” and a server representing the application server.
The threat model defines the “Improper Privilege Escalation” threat and includes attack paths such as “Exploiting Vulnerability” by the attacker and “Abusing User Privileges” by the user.
The code generates a threat model diagram in PNG format, named “improper_privilege_escalation_threat_model.png.”
from pytm import TM, Actor, Server
# Create a new threat model
tm = TM("Improper Privilege Escalation Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create server
server = Server("Application Server")
# Define improper privilege escalation threat
tm.add_threat()
tm.threat.name("Improper Privilege Escalation")
tm.threat.description("Threat of improper privilege escalation in the application")
# Define attack paths
tm.attack_path(attacker, server, "Exploiting Vulnerability")
tm.attack_path(user, server, "Abusing User Privileges")
# Generate the threat model diagram
tm.generate_diagram("improper_privilege_escalation_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Improper Privilege Escalation:
Concepts:
- Privilege Escalation: Unauthorized elevation of access privileges to perform actions beyond the authorized scope.
- Authorization Levels: Different levels of access privileges granted to users or roles.
- Insufficient Privilege Checks: Inadequate validation of user permissions when executing privileged actions.
- Unauthorized Actions: Performing actions that are not authorized or exceeding the granted privileges.
Users:
1. Attackers:
- Threat: Unauthorized Privilege Escalation
- Attempts to exploit vulnerabilities to gain higher levels of access privileges and perform unauthorized actions.
2. System Administrator:
- Threat: Misconfiguration of Privilege Levels
- Misconfigures access controls or fails to properly assign and manage privilege levels.
3. User:
- Threat: Unauthorized Access to Privileged Actions
- Attempts to perform actions beyond their authorized scope by exploiting privilege escalation vulnerabilities.
Components:
1. User Roles:
- Represent different roles or user groups with distinct privilege levels.
- Data Flow: Assignment of roles and associated permissions.
2. Privilege Validation:
- Validates user permissions before executing privileged actions.
- Data Flow: User permissions check and authorization decision.
Interactions:
1. Attackers:
- Exploits vulnerabilities or weaknesses to gain higher levels of access privileges.
- Performs unauthorized actions by bypassing or manipulating privilege validation mechanisms.
2. System Administrator:
- Misconfigures privilege levels, granting excessive permissions or failing to properly assign roles.
- Fails to implement proper privilege validation mechanisms or neglects regular review and updates.
3. User:
- Requests to perform actions within their authorized privileges.
- May attempt to escalate privileges by exploiting vulnerabilities in the system.
4. User Roles:
- Define the access privileges associated with different user groups or roles.
- Assigns and manages roles based on user responsibilities and organizational policies.
5. Privilege Validation:
- Validates user permissions before allowing execution of privileged actions.
- May have vulnerabilities or lack proper checks, enabling unauthorized privilege escalation.
Data leakage or unauthorized access
PyTM
This code creates a threat model using PyTM and represents the “Data Leakage or Unauthorized Access” threat scenario. It includes actors such as “Attacker” and “User” and a datastore representing sensitive data.
The threat model defines the “Data Leakage or Unauthorized Access” threat and includes attack paths such as “Exploiting Vulnerability” by the attacker and “Unauthorized Access” by the user.
The code generates a threat model diagram in PNG format, named “data_leakage_unauthorized_access_threat_model.png.”
from pytm import TM, Actor, Datastore
# Create a new threat model
tm = TM("Data Leakage or Unauthorized Access Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create datastore
datastore = Datastore("Sensitive Data")
# Define data leakage or unauthorized access threat
tm.add_threat()
tm.threat.name("Data Leakage or Unauthorized Access")
tm.threat.description("Threat of unauthorized access or leakage of sensitive data")
# Define attack paths
tm.attack_path(attacker, datastore, "Exploiting Vulnerability")
tm.attack_path(user, datastore, "Unauthorized Access")
# Generate the threat model diagram
tm.generate_diagram("data_leakage_unauthorized_access_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Data Leakage or Unauthorized Access:
Concepts:
- Data Leakage: Unintentional or unauthorized disclosure of sensitive data to unauthorized parties.
- Unauthorized Access: Gaining access to data or systems without proper authorization.
- Data Encryption: Process of converting sensitive data into a format that is unreadable without the appropriate decryption key.
- Data Loss Prevention (DLP): Techniques and controls implemented to prevent the leakage of sensitive data.
Users:
1. Attackers:
- Threat: Unauthorized Access or Data Leakage
- Attempts to gain unauthorized access to sensitive data or exploit vulnerabilities to leak data.
2. System Administrator:
- Threat: Misconfiguration of Access Controls or Encryption
- Misconfigures access controls, leaving data vulnerable to unauthorized access.
- Fails to implement or properly configure data encryption mechanisms.
3. User:
- Threat: Accidental Data Leakage
- Unintentionally exposes sensitive data through insecure practices or misconfigurations.
Components:
1. Data Storage:
- Represents storage systems or databases containing sensitive data.
- Data Flow: Storage and retrieval of sensitive data.
2. Access Controls:
- Mechanisms to control and enforce authorized access to data.
- Data Flow: Authentication and authorization checks.
3. Data Encryption:
- Techniques and algorithms used to protect sensitive data by encrypting it.
- Data Flow: Encryption and decryption processes.
4. Data Loss Prevention (DLP):
- Techniques and controls to prevent unauthorized data leakage.
- Data Flow: Data leakage prevention measures and monitoring.
Interactions:
1. Attackers:
- Exploits vulnerabilities to gain unauthorized access to sensitive data.
- May use various techniques to extract and exfiltrate the data without detection.
2. System Administrator:
- Misconfigures access controls, granting unauthorized users access to sensitive data.
- Fails to implement or properly configure data encryption, leaving data vulnerable to unauthorized access.
3. User:
- May accidentally expose sensitive data through insecure practices, such as sharing or mishandling information.
4. Data Storage:
- Stores sensitive data and requires robust access controls and encryption to protect it.
- May be vulnerable to unauthorized access if misconfigured or lacking proper security measures.
5. Access Controls:
- Enforces authorized access to data based on authentication and authorization checks.
- Misconfigurations or vulnerabilities in access controls may result in unauthorized access.
6. Data Encryption:
- Protects sensitive data by converting it into an unreadable format without the decryption key.
- Proper implementation and configuration of encryption algorithms are necessary to safeguard the data.
7. Data Loss Prevention (DLP):
- Implements techniques and controls to prevent unauthorized data leakage.
- Monitors data flows and applies policies to detect and prevent potential data leakage incidents.
Insecure data storage
PyTM
This code creates a threat model using PyTM and represents the “Insecure Data Storage” threat scenario. It includes actors such as “Attacker” and “User” and a datastore representing sensitive data.
The threat model defines the “Insecure Data Storage” threat and includes attack paths such as “Exploiting Storage Vulnerability” by the attacker and “Unauthorized Access to Stored Data” by the user.
The code generates a threat model diagram in PNG format, named “insecure_data_storage_threat_model.png.”
from pytm import TM, Actor, Datastore
# Create a new threat model
tm = TM("Insecure Data Storage Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create datastore
datastore = Datastore("Sensitive Data")
# Define insecure data storage threat
tm.add_threat()
tm.threat.name("Insecure Data Storage")
tm.threat.description("Threat of insecure storage of sensitive data")
# Define attack paths
tm.attack_path(attacker, datastore, "Exploiting Storage Vulnerability")
tm.attack_path(user, datastore, "Unauthorized Access to Stored Data")
# Generate the threat model diagram
tm.generate_diagram("insecure_data_storage_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Insecure Data Storage:
Concepts:
- Insecure Data Storage: Storing sensitive data in an unprotected or vulnerable manner.
- Data Encryption: Process of converting sensitive data into a format that is unreadable without the appropriate decryption key.
- Data Leakage: Unintentional or unauthorized disclosure of sensitive data.
- Data Access Controls: Mechanisms used to control and enforce authorized access to data.
Users:
1. Attackers:
- Threat: Unauthorized Data Access or Data Leakage
- Attempts to gain unauthorized access to sensitive data or exploit vulnerabilities to leak data.
2. System Administrator:
- Threat: Misconfiguration of Data Storage Security
- Misconfigures data storage settings, leaving sensitive data vulnerable to unauthorized access.
- Fails to implement or properly configure data encryption mechanisms.
3. User:
- Threat: Accidental Data Leakage
- Unintentionally exposes sensitive data through insecure practices or misconfigurations.
Components:
1. Data Storage:
- Represents storage systems or databases where sensitive data is stored.
- Data Flow: Storage and retrieval of sensitive data.
2. Data Encryption:
- Techniques and algorithms used to protect sensitive data by encrypting it.
- Data Flow: Encryption and decryption processes.
3. Data Access Controls:
- Mechanisms used to control and enforce authorized access to data.
- Data Flow: Authentication and authorization checks.
Interactions:
1. Attackers:
- Exploits vulnerabilities to gain unauthorized access to sensitive data.
- May use various techniques to extract and exfiltrate the data without detection.
2. System Administrator:
- Misconfigures data storage security settings, granting unauthorized users access to sensitive data.
- Fails to implement or properly configure data encryption mechanisms, leaving data vulnerable to unauthorized access.
3. User:
- May accidentally expose sensitive data through insecure practices, such as sharing or mishandling information.
4. Data Storage:
- Stores sensitive data and requires robust security measures to protect it.
- May be vulnerable to unauthorized access if misconfigured or lacking proper security controls.
5. Data Encryption:
- Protects sensitive data by converting it into an unreadable format without the decryption key.
- Proper implementation and configuration of encryption algorithms are necessary to safeguard the data.
6. Data Access Controls:
- Enforces authorized access to data based on authentication and authorization checks.
- Misconfigurations or vulnerabilities in access controls may result in unauthorized access.
Inadequate network segmentation
PyTM
This code creates a threat model using PyTM and represents the “Inadequate Network Segmentation” threat scenario. It includes actors such as “Attacker,” “Internal User,” and “External User,” and defines boundaries for the internal and external networks.
The threat model defines the “Inadequate Network Segmentation” threat and includes dataflows representing the flow of sensitive data, unauthorized access, exfiltration of sensitive data, and command and control.
The code generates a threat model diagram in PNG format, named “inadequate_network_segmentation_threat_model.png.”
from pytm import TM, Actor, Dataflow, Boundary
# Create a new threat model
tm = TM("Inadequate Network Segmentation Threat Model")
# Create actors
attacker = Actor("Attacker")
internalUser = Actor("Internal User")
externalUser = Actor("External User")
# Create boundaries
internalNetwork = Boundary("Internal Network")
externalNetwork = Boundary("External Network")
# Define dataflows
dataflow1 = Dataflow(internalUser, internalNetwork, "Sensitive Data Flow")
dataflow2 = Dataflow(externalUser, internalNetwork, "Unauthorized Access")
dataflow3 = Dataflow(internalNetwork, externalNetwork, "Exfiltration of Sensitive Data")
dataflow4 = Dataflow(internalNetwork, externalNetwork, "Command and Control")
# Define inadequate network segmentation threat
tm.add_threat()
tm.threat.name("Inadequate Network Segmentation")
tm.threat.description("Threat of inadequate segmentation between internal and external networks")
# Define attack paths
tm.attack_path(attacker, dataflow2, "Exploiting Insufficient Segmentation")
tm.attack_path(attacker, dataflow3, "Exfiltration of Sensitive Data")
tm.attack_path(attacker, dataflow4, "Command and Control")
# Generate the threat model diagram
tm.generate_diagram("inadequate_network_segmentation_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Inadequate Network Segmentation:
Concepts:
- Network Segmentation: Dividing a network into smaller, isolated segments to enhance security and control access.
- Inadequate Network Segmentation: Insufficient or improper separation of network segments, allowing unauthorized access or lateral movement.
- Network Firewall: A security device that monitors and filters network traffic based on predetermined security rules.
- Data Flow: The movement of data between different network segments.
Users:
1. Attackers:
- Threat: Unauthorized Access or Lateral Movement
- Attempts to gain unauthorized access to sensitive data or systems within different network segments.
- Exploits weaknesses in network segmentation to move laterally and escalate privileges.
2. System Administrator:
- Threat: Misconfiguration of Network Segmentation
- Misconfigures network segmentation rules, allowing unauthorized access between network segments.
- Fails to implement proper firewall rules to restrict network traffic.
Components:
1. Network Segments:
- Represents isolated network segments within the infrastructure.
- Data Flow: Controlled exchange of data between segments.
2. Network Firewall:
- Security device placed at the boundaries between network segments.
- Controls inbound and outbound network traffic based on predetermined rules.
- Data Flow: Filtering and routing of network traffic.
Interactions:
1. Attackers:
- Exploit weaknesses in network segmentation to gain unauthorized access to sensitive data or systems.
- May attempt lateral movement within the network, exploiting inadequate segmentation.
2. System Administrator:
- Misconfigures network segmentation rules, allowing unauthorized access between network segments.
- Fails to properly configure firewall rules, resulting in ineffective traffic filtering and segmentation.
3. Network Segments:
- Represent isolated segments within the network infrastructure.
- Require proper configuration and segmentation rules to ensure authorized access and prevent unauthorized movement.
4. Network Firewall:
- Controls the flow of network traffic between segments based on predefined security rules.
- Misconfiguration or inadequate rule set may lead to unauthorized access or lateral movement.
Man-in-the-Middle attacks
PyTM
This code creates a threat model using PyTM and represents the “Man-in-the-Middle (MitM) Attacks” threat scenario. It includes actors such as “Attacker,” “Client,” and “Server,” and defines boundaries for the client and server components.
The threat model defines the “Man-in-the-Middle Attacks” threat and includes a dataflow representing the flow of sensitive data between the client and server.
The code generates a threat model diagram in PNG format, named “man_in_the_middle_attacks_threat_model.png.”
from pytm import TM, Actor, Dataflow, Boundary
# Create a new threat model
tm = TM("Man-in-the-Middle Attacks Threat Model")
# Create actors
attacker = Actor("Attacker")
client = Actor("Client")
server = Actor("Server")
# Create boundaries
clientBoundary = Boundary("Client Boundary")
serverBoundary = Boundary("Server Boundary")
# Define dataflows
dataflow1 = Dataflow(client, server, "Sensitive Data Flow")
# Define Man-in-the-Middle attack threat
tm.add_threat()
tm.threat.name("Man-in-the-Middle (MitM) Attacks")
tm.threat.description("Threat of an attacker intercepting and tampering with communication between client and server")
# Define attack paths
tm.attack_path(attacker, dataflow1, "Intercepting and Tampering with Communication")
# Generate the threat model diagram
tm.generate_diagram("man_in_the_middle_attacks_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Man-in-the-Middle (MitM) Attacks:
Concepts:
- Man-in-the-Middle (MitM) Attack: A type of attack where an attacker intercepts communication between two parties to eavesdrop, modify, or inject malicious content.
- Network Traffic Encryption: The process of encrypting network traffic to protect it from unauthorized interception or tampering.
- Secure Communication Protocols: Protocols that provide secure and authenticated communication channels.
- Data Flow: The exchange of data between communicating parties.
Users:
1. Attackers:
- Threat: Intercept and Manipulate Communication
- Attempts to intercept network traffic between two parties and manipulate the data being transmitted.
- Uses various techniques, such as ARP spoofing or DNS spoofing, to position themselves as a "man in the middle."
2. System Administrator:
- Threat: Misconfiguration of Security Controls
- Fails to properly configure network security controls, allowing attackers to exploit vulnerabilities and perform MitM attacks.
- Does not enforce the use of secure communication protocols or encryption mechanisms.
3. Users:
- Threat: Unencrypted Communication
- Engage in communication without proper encryption or secure communication protocols.
- May unknowingly connect to compromised networks or fall victim to MitM attacks.
Components:
1. Communication Channel:
- Represents the medium through which parties communicate, such as network connections or wireless networks.
- Data Flow: Transmission of data between communicating parties.
2. Secure Communication Protocols:
- Protocols that provide secure and authenticated communication channels, such as HTTPS, SSL/TLS, or VPN.
- Data Flow: Encrypted transmission of data between parties.
Interactions:
1. Attackers:
- Position themselves as a "man in the middle" by intercepting and manipulating network traffic.
- Exploit vulnerabilities in the communication channel or lack of encryption to eavesdrop, modify, or inject malicious content.
2. System Administrator:
- Misconfigures network security controls, leaving communication channels vulnerable to MitM attacks.
- Fails to enforce the use of secure communication protocols or encryption mechanisms.
3. Users:
- Engage in communication without using secure communication protocols or encryption.
- May unknowingly connect to compromised networks or fall victim to MitM attacks.
4. Communication Channel:
- Represents the medium through which parties communicate.
- Vulnerable to interception and manipulation by attackers positioned as a "man in the middle."
5. Secure Communication Protocols:
- Provide secure and authenticated communication channels.
- Encryption and proper configuration of these protocols protect against MitM attacks.
Resource exhaustion
PyTM
This code creates a threat model using PyTM and represents the “Resource Exhaustion” threat scenario. It includes actors such as “Attacker” and “Service” and defines a dataflow between them.
The threat model defines the “Resource Exhaustion” threat and includes an attack path representing the attacker’s ability to consume excessive resources, leading to service availability impact.
The code generates a threat model diagram in PNG format, named “resource_exhaustion_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Resource Exhaustion Threat Model")
# Create actors
attacker = Actor("Attacker")
service = Actor("Service")
# Define dataflows
dataflow = Dataflow(attacker, service, "Data Flow")
# Define Resource Exhaustion threat
tm.add_threat()
tm.threat.name("Resource Exhaustion")
tm.threat.description("Threat of an attacker consuming excessive resources and impacting service availability")
# Define attack paths
tm.attack_path(attacker, dataflow, "Excessive Resource Consumption")
# Generate the threat model diagram
tm.generate_diagram("resource_exhaustion_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Resource Exhaustion:
Concepts:
- Resource Exhaustion: A type of attack where an attacker consumes excessive resources, such as CPU, memory, disk space, or network bandwidth, leading to service disruption or denial of service.
- System Resources: Refers to the various computing resources available within a system, including CPU, memory, disk space, and network bandwidth.
- Resource Management: The process of efficiently allocating and managing system resources.
- Data Flow: The movement of data or requests that require system resources.
Users:
1. Attackers:
- Threat: Resource Consumption
- Attempt to consume excessive system resources to cause service disruption or denial of service.
- Exploit vulnerabilities or design weaknesses to exhaust system resources.
2. System Administrators:
- Threat: Inadequate Resource Management
- Fail to implement proper resource management techniques, allowing attackers to consume resources beyond their normal limits.
- Lack monitoring and control mechanisms to detect and mitigate resource exhaustion attacks.
Components:
1. System Resources:
- Represents the various computing resources within a system, including CPU, memory, disk space, and network bandwidth.
- Data Flow: Requests or operations that require system resources.
2. Resource Management:
- Techniques and mechanisms employed to efficiently allocate and manage system resources.
- Data Flow: Allocation and utilization of system resources.
Interactions:
1. Attackers:
- Conduct resource exhaustion attacks by overwhelming system resources.
- Exploit vulnerabilities or design weaknesses to maximize resource consumption.
2. System Administrators:
- Implement resource management techniques to prevent resource exhaustion attacks.
- Monitor resource usage and detect abnormal resource consumption patterns.
3. System Resources:
- Available computing resources required for normal system operation.
- Can be overwhelmed and exhausted by attackers consuming excessive resources.
4. Resource Management:
- Controls and manages the allocation of system resources.
- Ensures efficient utilization and prevents resource exhaustion.
Distributed DoS (DDoS) attacks
PyTM
This code creates a threat model using PyTM and represents the “Distributed Denial of Service (DDoS) Attacks” threat scenario. It includes actors such as “Attacker” and “Target” and defines a dataflow between them.
The threat model defines the “DDoS Attacks” threat and includes an attack path representing the attacker overwhelming the target system with a high volume of requests, causing denial of service.
The code generates a threat model diagram in PNG format, named “ddos_attacks_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("DDoS Attacks Threat Model")
# Create actors
attacker = Actor("Attacker")
target = Actor("Target")
# Define dataflows
dataflow = Dataflow(attacker, target, "Data Flow")
# Define DDoS Attacks threat
tm.add_threat()
tm.threat.name("DDoS Attacks")
tm.threat.description("Threat of an attacker overwhelming the target system with a high volume of requests, causing denial of service")
# Define attack paths
tm.attack_path(attacker, dataflow, "DDoS Attack")
# Generate the threat model diagram
tm.generate_diagram("ddos_attacks_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Distributed Denial of Service (DDoS) Attacks:
Concepts:
- Distributed Denial of Service (DDoS) Attack: A type of attack where multiple compromised systems, known as "botnets," flood a target system with a high volume of traffic or requests, overwhelming its resources and causing service disruption or denial of service.
- Botnet: A network of compromised computers or devices under the control of an attacker, used to launch DDoS attacks.
- Traffic Amplification: Techniques used by attackers to magnify the volume of traffic generated by each compromised system in the botnet.
- Resource Consumption: The depletion of system resources, such as network bandwidth, CPU, memory, or storage, due to the high volume of incoming traffic or requests.
Users:
1. Attackers:
- Threat: DDoS Attack
- Control a botnet comprising multiple compromised systems.
- Coordinate the attack to flood the target system with a high volume of traffic or requests, causing service disruption or denial of service.
- Use traffic amplification techniques to maximize the impact of the attack.
2. Target System:
- Threat: Service Disruption or Denial of Service
- Represents the system or service under attack.
- Receives a massive influx of traffic or requests from the botnet, causing resource exhaustion and rendering the system inaccessible.
Components:
1. Botnet:
- Collection of compromised systems under the control of the attacker.
- Data Flow: Communication and coordination between the attacker and compromised systems for launching the DDoS attack.
2. Traffic Amplification Techniques:
- Methods used by attackers to increase the volume of traffic generated by each compromised system.
- Data Flow: Manipulation of traffic to amplify its volume before being directed to the target system.
3. Target System:
- Represents the system or service being targeted by the DDoS attack.
- Data Flow: Incoming traffic or requests that overwhelm the system's resources.
Interactions:
1. Attackers:
- Control the botnet and orchestrate the DDoS attack.
- Utilize traffic amplification techniques to maximize the impact of the attack.
2. Botnet:
- Comprises compromised systems under the control of the attackers.
- Executes instructions from the attackers to generate and direct a high volume of traffic or requests to the target system.
3. Traffic Amplification Techniques:
- Used by attackers to increase the volume of traffic generated by each compromised system.
- Amplify the traffic before it reaches the target system, magnifying the impact of the DDoS attack.
4. Target System:
- Represents the system or service under attack.
- Overwhelmed by the high volume of incoming traffic or requests, leading to resource exhaustion and service disruption or denial of service.
Misconfigured security settings
PyTM
This code creates a threat model using PyTM and represents the “Misconfigured Security Settings” threat scenario. It includes actors such as “Administrator” and “Attacker” and defines a dataflow between them.
The threat model defines the “Misconfigured Security Settings” threat and describes the threat arising from misconfigured security settings, leading to vulnerabilities and potential unauthorized access.
The code generates a threat model diagram in PNG format, named “misconfigured_security_settings_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Misconfigured Security Settings Threat Model")
# Create actors
administrator = Actor("Administrator")
attacker = Actor("Attacker")
# Define dataflows
dataflow = Dataflow(administrator, attacker, "Data Flow")
# Define Misconfigured Security Settings threat
tm.add_threat()
tm.threat.name("Misconfigured Security Settings")
tm.threat.description("Threat arising from misconfigured security settings, leading to vulnerabilities and potential unauthorized access")
# Define attack paths
tm.attack_path(administrator, dataflow, "Misconfiguration Attack")
# Generate the threat model diagram
tm.generate_diagram("misconfigured_security_settings_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Misconfigured Security Settings:
Concepts:
- Misconfigured Security Settings: Configuration settings that do not adhere to recommended security practices, leaving systems or components vulnerable to attacks or unauthorized access.
- Security Configuration: The settings and configurations applied to systems, applications, or network components to enforce security controls and protect against threats.
- Attack Surface: The collection of entry points or vulnerabilities that can be exploited by attackers to gain unauthorized access or compromise a system.
- Attack Path: The path or sequence of steps an attacker can take to exploit misconfigured security settings and compromise the system.
Users:
1. System Administrators:
- Threat: Inadequate Configuration
- Responsible for configuring and managing security settings of systems, applications, or network components.
- May inadvertently misconfigure security settings, leaving vulnerabilities or weak points open to exploitation.
2. Attackers:
- Threat: Unauthorized Access or Exploitation
- Attempt to exploit misconfigured security settings to gain unauthorized access, escalate privileges, or compromise the system.
- Exploit weaknesses in security configurations to bypass controls and launch attacks.
Components:
1. System or Application:
- Represents the system or application with security settings that need to be configured correctly.
- Contains various security-related configurations that affect the overall security posture.
2. Security Configuration Settings:
- Specific settings or configurations applied to systems, applications, or network components to enforce security controls.
- Include settings related to authentication, access controls, encryption, logging, auditing, and other security measures.
Interactions:
1. System Administrators:
- Responsible for configuring and managing security settings.
- May misconfigure security settings, leaving vulnerabilities or weak points open to exploitation by attackers.
2. Attackers:
- Attempt to exploit misconfigured security settings to gain unauthorized access or compromise the system.
- Exploit weaknesses in security configurations to bypass controls and launch attacks.
3. System or Application:
- Contains security configurations that need to be correctly applied and managed.
- Vulnerable to attacks and unauthorized access if security settings are misconfigured.
4. Attack Surface:
- Represents the collection of entry points or vulnerabilities that attackers can exploit.
- Misconfigured security settings may increase the attack surface and provide opportunities for exploitation.
5. Attack Path:
- Represents the sequence of steps an attacker can take to exploit misconfigured security settings.
- Follows the path of least resistance to compromise the system or gain unauthorized access.
Insecure default configurations
PyTM
This code creates a threat model using PyTM and represents the “Insecure Default Configurations” threat scenario. It includes actors such as “Administrator” and “Attacker” and defines a dataflow between them.
The threat model defines the “Insecure Default Configurations” threat and describes the threat arising from insecure default configurations, leading to vulnerabilities and potential unauthorized access.
The code generates a threat model diagram in PNG format, named “insecure_default_configurations_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Insecure Default Configurations Threat Model")
# Create actors
administrator = Actor("Administrator")
attacker = Actor("Attacker")
# Define dataflows
dataflow = Dataflow(administrator, attacker, "Data Flow")
# Define Insecure Default Configurations threat
tm.add_threat()
tm.threat.name("Insecure Default Configurations")
tm.threat.description("Threat arising from insecure default configurations, leading to vulnerabilities and potential unauthorized access")
# Define attack paths
tm.attack_path(administrator, dataflow, "Insecure Default Configurations Attack")
# Generate the threat model diagram
tm.generate_diagram("insecure_default_configurations_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Insecure Default Configurations:
Concepts:
- Insecure Default Configurations: System or application configurations that are insecure or weak by default, often set during installation or initialization.
- Attack Surface: The collection of entry points or vulnerabilities that can be exploited by attackers to gain unauthorized access or compromise a system.
- Attack Path: The path or sequence of steps an attacker can take to exploit insecure default configurations and compromise the system.
Users:
1. System Administrators:
- Threat: Inadequate Configuration
- Responsible for setting up and configuring systems or applications.
- May unintentionally leave insecure default configurations in place, providing potential vulnerabilities to attackers.
2. Attackers:
- Threat: Unauthorized Access or Exploitation
- Attempt to exploit insecure default configurations to gain unauthorized access, escalate privileges, or compromise the system.
- Exploit weaknesses in default configurations to bypass security controls and launch attacks.
Components:
1. System or Application:
- Represents the system or application with default configurations that need to be changed.
- Contains various settings and configurations that impact security.
2. Default Configuration Settings:
- The initial settings or configurations that are in place when a system or application is installed or initialized.
- These configurations may not provide adequate security and need to be modified to reduce vulnerabilities.
Interactions:
1. System Administrators:
- Responsible for setting up and configuring systems or applications.
- May overlook or neglect changing insecure default configurations, leaving potential vulnerabilities for attackers.
2. Attackers:
- Attempt to exploit insecure default configurations to gain unauthorized access or compromise the system.
- Exploit weaknesses in default configurations to bypass security controls and launch attacks.
3. System or Application:
- Contains default configurations that need to be changed to reduce vulnerabilities.
- Vulnerable to attacks and unauthorized access if insecure default configurations are not addressed.
4. Attack Surface:
- Represents the collection of entry points or vulnerabilities that attackers can exploit.
- Insecure default configurations may increase the attack surface and provide opportunities for exploitation.
5. Attack Path:
- Represents the sequence of steps an attacker can take to exploit insecure default configurations.
- Follows the path of least resistance to compromise the system or gain unauthorized access.
Delayed patching of software
PyTM
This code creates a threat model using PyTM and represents the “Delayed Patching of Software” threat scenario. It includes actors such as “Administrator” and “Attacker” and defines a dataflow between them.
The threat model defines the “Delayed Patching of Software” threat and describes the threat arising from delayed or inadequate software patching, leaving systems vulnerable to known exploits.
The code generates a threat model diagram in PNG format, named “delayed_patching_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Delayed Patching of Software Threat Model")
# Create actors
administrator = Actor("Administrator")
attacker = Actor("Attacker")
# Define dataflows
dataflow = Dataflow(administrator, attacker, "Data Flow")
# Define Delayed Patching of Software threat
tm.add_threat()
tm.threat.name("Delayed Patching of Software")
tm.threat.description("Threat arising from delayed or inadequate software patching, leaving systems vulnerable to known exploits")
# Define attack paths
tm.attack_path(administrator, dataflow, "Delayed Patching of Software Attack")
# Generate the threat model diagram
tm.generate_diagram("delayed_patching_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Delayed Patching of Software:
Concepts:
- Delayed Patching of Software: The practice of not applying patches and updates promptly to software or systems, leaving them vulnerable to known security vulnerabilities.
- Attack Surface: The collection of entry points or vulnerabilities that can be exploited by attackers to gain unauthorized access or compromise a system.
- Attack Path: The path or sequence of steps an attacker can take to exploit the delayed patching of software and compromise the system.
Users:
1. System Administrators:
- Threat: Inadequate Patch Management
- Responsible for managing and applying patches and updates to software or systems.
- May delay or neglect applying patches promptly, leaving vulnerabilities open for exploitation.
2. Attackers:
- Threat: Exploitation of Known Vulnerabilities
- Attempt to exploit known vulnerabilities in software or systems that have not been patched promptly.
- Exploit weaknesses in unpatched software to gain unauthorized access, escalate privileges, or compromise the system.
Components:
1. Software or System:
- Represents the software or system that requires regular patching and updates.
- Contains known vulnerabilities that can be addressed through patching.
2. Patch Management Process:
- The process of managing and applying patches and updates to software or systems.
- Includes tasks such as patch assessment, testing, deployment, and monitoring.
Interactions:
1. System Administrators:
- Responsible for managing and applying patches and updates to software or systems.
- May delay or neglect applying patches promptly due to operational constraints or other reasons.
2. Attackers:
- Attempt to exploit known vulnerabilities in unpatched software or systems.
- Exploit weaknesses in software that has not been updated to gain unauthorized access or compromise the system.
3. Software or System:
- Requires regular patching and updates to address known vulnerabilities.
- Vulnerable to attacks and unauthorized access if patches are not applied promptly.
4. Attack Surface:
- Represents the collection of entry points or vulnerabilities that attackers can exploit.
- Delayed patching of software may increase the attack surface and provide opportunities for exploitation.
5. Attack Path:
- Represents the sequence of steps an attacker can take to exploit delayed patching of software.
- Follows the path of least resistance to compromise the system or gain unauthorized access.
Note: This simplified textual representation provides a high-level view of the components, data flows, and interactions related to the "Delayed Patching of Software" threat. In a comprehensive threat model, additional specific components and interactions relevant to the system being analyzed would be included.
Lack of vulnerability scanning
PyTM
This code creates a threat model using PyTM and represents the “Lack of Vulnerability Scanning” threat scenario. It includes actors such as “Administrator” and “Attacker” and defines a dataflow between them.
The threat model defines the “Lack of Vulnerability Scanning” threat and describes the threat arising from the lack of regular vulnerability scanning, which can result in undetected vulnerabilities and potential exploitation.
The code generates a threat model diagram in PNG format, named “lack_of_vulnerability_scanning_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Lack of Vulnerability Scanning Threat Model")
# Create actors
administrator = Actor("Administrator")
attacker = Actor("Attacker")
# Define dataflows
dataflow = Dataflow(administrator, attacker, "Data Flow")
# Define Lack of Vulnerability Scanning threat
tm.add_threat()
tm.threat.name("Lack of Vulnerability Scanning")
tm.threat.description("Threat arising from the lack of regular vulnerability scanning, which can result in undetected vulnerabilities and potential exploitation")
# Define attack paths
tm.attack_path(administrator, dataflow, "Lack of Vulnerability Scanning Attack")
# Generate the threat model diagram
tm.generate_diagram("lack_of_vulnerability_scanning_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Lack of Vulnerability Scanning:
Concepts:
- Lack of Vulnerability Scanning: Failure to regularly scan systems or applications for known vulnerabilities and weaknesses.
- Vulnerability Assessment: The process of identifying and assessing vulnerabilities within systems or applications.
- Attack Surface: The collection of entry points or vulnerabilities that can be exploited by attackers to gain unauthorized access or compromise a system.
- Attack Path: The path or sequence of steps an attacker can take to exploit existing vulnerabilities and compromise the system.
Users:
1. System Administrators:
- Responsible for managing and maintaining systems or applications.
- May neglect or overlook the importance of regular vulnerability scanning.
2. Attackers:
- Threat: Exploitation of Unpatched Vulnerabilities
- Attempt to identify and exploit unpatched vulnerabilities in systems or applications.
- Exploit weaknesses that have not been detected due to the lack of vulnerability scanning.
Components:
1. System or Application:
- Represents the system or application that requires regular vulnerability scanning.
- Contains potential vulnerabilities that need to be identified and mitigated.
2. Vulnerability Scanning Tool:
- A tool or software used to scan systems or applications for known vulnerabilities.
- Detects and reports on potential weaknesses that could be exploited by attackers.
Interactions:
1. System Administrators:
- Responsible for managing and maintaining systems or applications.
- May fail to prioritize or schedule regular vulnerability scanning, leaving systems exposed to unpatched vulnerabilities.
2. Attackers:
- Attempt to identify and exploit unpatched vulnerabilities in systems or applications.
- Exploit weaknesses that have not been detected due to the lack of vulnerability scanning.
3. System or Application:
- Requires regular vulnerability scanning to identify and mitigate potential vulnerabilities.
- Vulnerable to attacks and unauthorized access if unpatched vulnerabilities are not detected and addressed.
4. Attack Surface:
- Represents the collection of entry points or vulnerabilities that attackers can exploit.
- Lack of vulnerability scanning may increase the attack surface and provide opportunities for exploitation.
5. Attack Path:
- Represents the sequence of steps an attacker can take to exploit unpatched vulnerabilities.
- Follows the path of least resistance to compromise the system or gain unauthorized access.
Malicious or negligent insiders
PyTM
This code creates a threat model using PyTM and represents the “Malicious or Negligent Insiders” threat scenario. It includes actors such as “Insider” and “Attacker” and defines a dataflow between them.
The threat model defines the “Malicious or Negligent Insiders” threat and describes the threat arising from insiders with malicious intent or negligent behavior who may abuse their privileges, steal sensitive data, or cause damage to the system.
The code generates a threat model diagram in PNG format, named “malicious_or_negligent_insiders_threat_model.png.”
from pytm import TM, Actor, Dataflow
# Create a new threat model
tm = TM("Malicious or Negligent Insiders Threat Model")
# Create actors
insider = Actor("Insider")
attacker = Actor("Attacker")
# Define dataflows
dataflow = Dataflow(insider, attacker, "Data Flow")
# Define Malicious or Negligent Insiders threat
tm.add_threat()
tm.threat.name("Malicious or Negligent Insiders")
tm.threat.description("Threat arising from insiders with malicious intent or negligent behavior who may abuse their privileges, steal sensitive data, or cause damage to the system")
# Define attack paths
tm.attack_path(insider, dataflow, "Malicious or Negligent Insiders Attack")
# Generate the threat model diagram
tm.generate_diagram("malicious_or_negligent_insiders_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Malicious or Negligent Insiders:
Concepts:
- Insiders: Individuals who have authorized access to a system or application.
- Malicious Insider: An insider who intentionally abuses their privileges or acts with malicious intent.
- Negligent Insider: An insider who unintentionally causes harm or breaches security due to carelessness.
- Access Controls: Mechanisms used to enforce authorized access to resources.
- Data Loss or Leakage: Unauthorized disclosure or loss of sensitive data.
Users:
1. Malicious Insider:
- Threat: Unauthorized Access or Data Theft
- Exploits their authorized access to gain unauthorized access, steal data, or cause damage to the system.
2. Negligent Insider:
- Threat: Accidental Data Breach
- Unintentionally exposes sensitive data or breaches security due to carelessness or lack of awareness.
Components:
1. Authentication System:
- Manages user authentication and access controls.
- Data Flow: User authentication requests.
2. Data Storage:
- Stores sensitive data.
- Data Flow: Reading or modifying sensitive data.
3. Logging System:
- Captures logs and auditing information.
- Data Flow: Storing logs of user activities.
Interactions:
1. Malicious Insider:
- Exploits weak authentication controls or stolen credentials to gain unauthorized access to the system.
- Performs unauthorized data access or theft by bypassing access controls or abusing privileges.
2. Negligent Insider:
- Accidentally exposes sensitive data by misconfiguring access controls or mishandling data.
- May unknowingly download or transmit sensitive data to external sources.
3. Authentication System:
- Authenticates user credentials and enforces access controls.
- Logs authentication activities and detects suspicious login patterns.
4. Data Storage:
- Stores sensitive data and enforces access controls.
- Logs data access and modification activities.
5. Logging System:
- Captures logs of user activities, including authentication attempts and data access events.
- Supports monitoring and analysis to identify suspicious or unauthorized activities.
Unauthorized data access or theft
PyTM
This code creates a threat model using PyTM and represents the “Unauthorized Data Access or Theft” threat scenario. It includes actors such as “Attacker” and “User” and defines a dataflow between the user and a sensitive datastore.
The threat model defines the “Unauthorized Data Access or Theft” threat and describes the threat of unauthorized access or theft of sensitive data by attackers.
The code generates a threat model diagram in PNG format, named “unauthorized_data_access_theft_threat_model.png.”
from pytm import TM, Actor, Datastore, Boundary, Dataflow
# Create a new threat model
tm = TM("Unauthorized Data Access or Theft Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create a boundary
boundary = Boundary("Internal Network")
# Create a datastore
datastore = Datastore("Sensitive Data")
# Define dataflows
dataflow = Dataflow(user, datastore, "Data Access")
# Define Unauthorized Data Access or Theft threat
tm.add_threat()
tm.threat.name("Unauthorized Data Access or Theft")
tm.threat.description("Threat of unauthorized access or theft of sensitive data by attackers")
# Define attack paths
tm.attack_path(attacker, dataflow, "Unauthorized Data Access or Theft Attack")
# Generate the threat model diagram
tm.generate_diagram("unauthorized_data_access_theft_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Unauthorized Data Access or Theft:
Concepts:
- Unauthorized Data Access or Theft: The unauthorized access, theft, or disclosure of sensitive or confidential data.
- Data Classification: The process of categorizing data based on its sensitivity or criticality.
- Access Controls: Mechanisms and policies in place to regulate access to data and protect it from unauthorized access.
- Attack Surface: The collection of entry points or vulnerabilities that can be exploited by attackers to gain unauthorized access or compromise a system.
- Attack Path: The path or sequence of steps an attacker can take to exploit vulnerabilities and gain unauthorized access to data.
Users:
1. System Administrators:
- Responsible for managing access controls and permissions to sensitive data.
- May misconfigure or overlook security settings, leading to unauthorized access or theft.
2. Attackers:
- Threat: Unauthorized Data Access or Theft
- Attempt to gain unauthorized access to sensitive data or steal it for malicious purposes.
- Exploit vulnerabilities in access controls or other weaknesses to bypass security measures.
Components:
1. Sensitive Data:
- Represents the data that needs to be protected from unauthorized access or theft.
- Includes personally identifiable information (PII), financial data, intellectual property, or other confidential data.
2. Access Control Mechanisms:
- The mechanisms and policies in place to control access to sensitive data.
- Examples include user authentication, role-based access control (RBAC), and encryption.
Interactions:
1. System Administrators:
- Responsible for managing access controls and permissions to sensitive data.
- May misconfigure or overlook security settings, leading to unauthorized access or theft.
2. Attackers:
- Attempt to gain unauthorized access to sensitive data or steal it for malicious purposes.
- Exploit vulnerabilities in access controls or other weaknesses to bypass security measures.
3. Sensitive Data:
- Requires appropriate access controls to prevent unauthorized access or theft.
- Vulnerable to unauthorized access or theft if access controls are not properly implemented or misconfigured.
4. Attack Surface:
- Represents the collection of entry points or vulnerabilities that attackers can exploit.
- Weak or misconfigured access controls may increase the attack surface and provide opportunities for unauthorized access.
5. Attack Path:
- Represents the sequence of steps an attacker can take to exploit vulnerabilities and gain unauthorized access to sensitive data.
- Follows the path of least resistance to compromise the system and steal data.
Unauthorized physical access
PyTM
This code creates a threat model using PyTM and represents the “Unauthorized Physical Access” threat scenario. It includes actors such as “Attacker,” “Physical Attacker,” and “User” and defines a dataflow between the user and a sensitive equipment datastore.
The threat model defines the “Unauthorized Physical Access” threat and describes the threat of unauthorized physical access to sensitive equipment by attackers.
The code generates a threat model diagram in PNG format, named “unauthorized_physical_access_threat_model.png.”
from pytm import TM, Actor, Datastore, Boundary, Dataflow
# Create a new threat model
tm = TM("Unauthorized Physical Access Threat Model")
# Create actors
attacker = Actor("Attacker")
physical_attacker = Actor("Physical Attacker")
user = Actor("User")
# Create a boundary
boundary = Boundary("Physical Location")
# Create a datastore
datastore = Datastore("Sensitive Equipment")
# Define dataflows
dataflow = Dataflow(user, datastore, "Data Access")
# Define Unauthorized Physical Access threat
tm.add_threat()
tm.threat.name("Unauthorized Physical Access")
tm.threat.description("Threat of unauthorized physical access to sensitive equipment by attackers")
# Define attack paths
tm.attack_path(physical_attacker, dataflow, "Unauthorized Physical Access Attack")
# Generate the threat model diagram
tm.generate_diagram("unauthorized_physical_access_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Unauthorized Physical Access:
Concepts:
- Unauthorized Physical Access: The unauthorized entry or presence of individuals in physical areas where they should not be.
- Physical Security: Measures and controls implemented to protect physical assets, such as buildings, rooms, and equipment.
- Access Control: Mechanisms and policies in place to regulate entry and restrict access to physical areas.
- Attack Surface: Vulnerabilities and entry points that can be exploited by unauthorized individuals to gain physical access.
- Attack Path: The sequence of steps an attacker can take to bypass physical security measures and gain unauthorized access.
Users:
1. Facility Administrators:
- Responsible for managing physical security measures and access control systems.
- May misconfigure or overlook security settings, leading to unauthorized physical access.
2. Unauthorized Individuals:
- Threat: Unauthorized Physical Access
- Attempt to gain physical access to restricted areas without proper authorization.
- Exploit vulnerabilities in physical security measures or find ways to bypass them.
Components:
1. Physical Areas:
- Represents the different areas within a facility or premises, such as server rooms, data centers, or restricted zones.
- Each area has a designated level of access restriction and contains valuable assets or sensitive information.
2. Access Control Mechanisms:
- The mechanisms and controls in place to regulate entry and restrict access to physical areas.
- Examples include access cards, biometric systems, locks, alarms, and surveillance cameras.
Interactions:
1. Facility Administrators:
- Responsible for managing physical security measures and access control systems.
- May misconfigure or overlook security settings, leading to unauthorized physical access.
2. Unauthorized Individuals:
- Attempt to gain physical access to restricted areas without proper authorization.
- Exploit vulnerabilities in physical security measures or find ways to bypass them.
3. Physical Areas:
- Require proper access control mechanisms to prevent unauthorized physical access.
- Vulnerable to unauthorized access if physical security measures are not properly implemented or misconfigured.
4. Attack Surface:
- Represents the vulnerabilities and entry points that unauthorized individuals can exploit.
- Weak or misconfigured physical security measures may increase the attack surface and provide opportunities for unauthorized physical access.
5. Attack Path:
- Represents the sequence of steps an attacker can take to bypass physical security measures and gain unauthorized access.
- Follows the path of least resistance to compromise the physical security of the facility or premises.
Theft or destruction of hardware
PyTM
This code creates a threat model using PyTM and represents the “Theft or Destruction of Hardware” threat scenario. It includes actors such as “Attacker,” “Physical Attacker,” and “User” and defines a dataflow between the user and a hardware datastore.
The threat model defines the “Theft or Destruction of Hardware” threat and describes the threat of theft or destruction of hardware by attackers.
The code generates a threat model diagram in PNG format, named “theft_destruction_hardware_threat_model.png.”
from pytm import TM, Actor, Datastore, Boundary, Dataflow
# Create a new threat model
tm = TM("Theft or Destruction of Hardware Threat Model")
# Create actors
attacker = Actor("Attacker")
physical_attacker = Actor("Physical Attacker")
user = Actor("User")
# Create a boundary
boundary = Boundary("Physical Location")
# Create a datastore
datastore = Datastore("Hardware")
# Define dataflows
dataflow = Dataflow(user, datastore, "Data Access")
# Define Theft or Destruction of Hardware threat
tm.add_threat()
tm.threat.name("Theft or Destruction of Hardware")
tm.threat.description("Threat of theft or destruction of hardware by attackers")
# Define attack paths
tm.attack_path(physical_attacker, dataflow, "Theft or Destruction of Hardware Attack")
# Generate the threat model diagram
tm.generate_diagram("theft_destruction_hardware_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Theft or Destruction of Hardware:
Concepts:
- Theft or Destruction of Hardware: The unauthorized removal or damage of physical hardware devices.
- Physical Security: Measures and controls implemented to protect physical assets, such as hardware devices.
- Asset Inventory: A record of all hardware devices, their locations, and ownership.
- Attack Surface: Vulnerabilities and entry points that can be exploited by unauthorized individuals to steal or damage hardware.
- Attack Path: The sequence of steps an attacker can take to bypass physical security measures and steal or destroy hardware.
Users:
1. Facility Administrators:
- Responsible for managing physical security measures and maintaining the asset inventory.
- May misconfigure or overlook security settings, leading to vulnerabilities in hardware protection.
2. Unauthorized Individuals:
- Threat: Theft or Destruction of Hardware
- Attempt to steal or damage hardware devices for personal gain, sabotage, or other malicious purposes.
- Exploit vulnerabilities in physical security measures or find ways to bypass them.
Components:
1. Hardware Devices:
- Represents the physical devices, such as servers, workstations, laptops, or other valuable equipment.
- Each device has its unique identification, location, and ownership information recorded in the asset inventory.
2. Physical Security Measures:
- The measures and controls in place to protect hardware devices from theft or destruction.
- Examples include locks, alarms, surveillance cameras, access control mechanisms, and secure storage areas.
3. Asset Inventory:
- A record or database that tracks all hardware devices, their locations, and ownership information.
- Helps identify missing or compromised hardware and aids in recovery or replacement processes.
Interactions:
1. Facility Administrators:
- Responsible for managing physical security measures and maintaining the asset inventory.
- May misconfigure or overlook security settings, leading to vulnerabilities in hardware protection.
2. Unauthorized Individuals:
- Attempt to steal or damage hardware devices for personal gain, sabotage, or other malicious purposes.
- Exploit vulnerabilities in physical security measures or find ways to bypass them.
3. Hardware Devices:
- Require proper physical security measures to prevent unauthorized access, theft, or destruction.
- Vulnerable to theft or destruction if physical security measures are not properly implemented or misconfigured.
4. Asset Inventory:
- Maintained by facility administrators to track hardware devices and ownership information.
- Helps in identifying missing or compromised hardware and aids in recovery or replacement processes.
5. Attack Surface:
- Represents the vulnerabilities and entry points that unauthorized individuals can exploit.
- Weak or misconfigured physical security measures may increase the attack surface and provide opportunities for theft or destruction of hardware.
6. Attack Path:
- Represents the sequence of steps an attacker can take to bypass physical security measures and steal or destroy hardware.
- Follows the path of least resistance to compromise the physical security of the hardware devices.
Vulnerabilities in third-party components
PyTM
This code creates a threat model using PyTM and represents the “Vulnerabilities in Third-Party Components” threat scenario. It includes actors such as “Attacker” and “User” and defines a dataflow between the user and a sensitive data datastore.
The threat model defines the “Vulnerabilities in Third-Party Components” threat and describes the threat of vulnerabilities in third-party components used in the system.
The code generates a threat model diagram in PNG format, named “third_party_component_vulnerabilities_threat_model.png.”
from pytm import TM, Actor, Datastore, Dataflow, Boundary
# Create a new threat model
tm = TM("Vulnerabilities in Third-Party Components Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
# Create a boundary
boundary = Boundary("System Boundary")
# Create a datastore
datastore = Datastore("Sensitive Data")
# Define dataflows
dataflow = Dataflow(user, datastore, "Data Access")
# Define Vulnerabilities in Third-Party Components threat
tm.add_threat()
tm.threat.name("Vulnerabilities in Third-Party Components")
tm.threat.description("Threat of vulnerabilities in third-party components used in the system")
# Define attack paths
tm.attack_path(attacker, dataflow, "Exploitation of Third-Party Component Vulnerabilities")
# Generate the threat model diagram
tm.generate_diagram("third_party_component_vulnerabilities_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Vulnerabilities in Third-Party Components:
Concepts:
- Vulnerabilities in Third-Party Components: Weaknesses or flaws present in software or hardware components developed by external third-party vendors.
- Third-Party Components: Software or hardware modules, libraries, frameworks, or services developed by external vendors and integrated into the system.
- Software Development Lifecycle (SDLC): The process of developing, testing, and deploying software.
- Vulnerability Management: The process of identifying, assessing, mitigating, and monitoring vulnerabilities in software components.
- Patch Management: The process of applying security patches and updates to third-party components.
Users:
1. System Developers:
- Responsible for integrating and using third-party components in the system.
- May unknowingly introduce vulnerabilities by not properly assessing the security of the components or by not implementing them correctly.
2. Third-Party Component Vendors:
- Develop and maintain the third-party components used in the system.
- May have vulnerabilities in their components due to coding errors, design flaws, or outdated dependencies.
Components:
1. Third-Party Components:
- Represents the software or hardware modules, libraries, frameworks, or services developed by external vendors and integrated into the system.
- Can introduce vulnerabilities if not properly assessed, implemented, or kept up to date with security patches.
2. System Components:
- Represents the internal components of the system, including the custom-developed software and other infrastructure elements.
3. Software Development Lifecycle (SDLC):
- The process followed by system developers to develop, test, and deploy the system.
- Involves activities such as requirements gathering, design, coding, testing, and deployment.
Interactions:
1. System Developers:
- Responsible for integrating and using third-party components in the system.
- Should assess the security of the third-party components before integration and ensure they are properly implemented.
2. Third-Party Component Vendors:
- Develop and maintain the third-party components used in the system.
- Should follow secure coding practices, conduct regular security assessments, and provide security patches and updates for their components.
3. Third-Party Components:
- Integrated into the system by system developers.
- Can introduce vulnerabilities if not properly assessed or implemented.
4. Software Development Lifecycle (SDLC):
- Provides a framework for system developers to follow during the development process.
- Should include security measures and assessments to identify and address vulnerabilities in third-party components.
5. Vulnerability Management:
- Involves identifying, assessing, mitigating, and monitoring vulnerabilities in software components.
- Should be part of the overall system development and maintenance processes.
6. Patch Management:
- Involves applying security patches and updates to third-party components to address known vulnerabilities.
- Should be performed regularly to keep the system protected against known vulnerabilities.
Lack of oversight on third-party activities
PyTM
This code creates a threat model using PyTM and represents the “Lack of Oversight on Third-Party Activities” threat scenario. It includes actors such as “Attacker,” “User,” and “Third-Party” and defines dataflows between the user, third-party process, and a sensitive data datastore.
The threat model defines the “Lack of Oversight on Third-Party Activities” threat and describes the threat of insufficient oversight on third-party activities in the system.
The code generates a threat model diagram in PNG format, named “lack_of_oversight_third_party_activities_threat_model.png.”
from pytm import TM, Actor, Process, Datastore, Dataflow, Boundary
# Create a new threat model
tm = TM("Lack of Oversight on Third-Party Activities Threat Model")
# Create actors
attacker = Actor("Attacker")
user = Actor("User")
third_party = Actor("Third-Party")
# Create a boundary
boundary = Boundary("System Boundary")
# Create a process
process = Process("Third-Party Process")
# Create a datastore
datastore = Datastore("Sensitive Data")
# Define dataflows
dataflow1 = Dataflow(user, process, "Data Sharing")
dataflow2 = Dataflow(process, datastore, "Data Storage")
# Define Lack of Oversight on Third-Party Activities threat
tm.add_threat()
tm.threat.name("Lack of Oversight on Third-Party Activities")
tm.threat.description("Threat of lack of oversight on third-party activities in the system")
# Define attack paths
tm.attack_path(attacker, dataflow1, "Unauthorized Data Sharing")
tm.attack_path(attacker, dataflow2, "Unauthorized Data Storage")
# Generate the threat model diagram
tm.generate_diagram("lack_of_oversight_third_party_activities_threat_model.png")
Microsoft Threat Model
Threat Model Diagram for Lack of Oversight on Third-Party Activities:
Concepts:
- Lack of Oversight: Insufficient monitoring, supervision, or control over the activities performed by third-party vendors.
- Third-Party Activities: Activities carried out by external vendors, such as software development, data processing, or system maintenance.
- Trust Boundaries: Points where the system interacts with external entities, including third-party vendors.
- Data Privacy: Protection of sensitive data from unauthorized access, use, or disclosure.
- Regulatory Compliance: Adherence to relevant laws, regulations, and industry standards.
Users:
1. System Owners:
- Responsible for overseeing the system's operations, security, and compliance.
- May delegate certain tasks or responsibilities to third-party vendors.
2. Third-Party Vendors:
- External entities engaged to perform specific activities or provide services related to the system.
- May have access to system components, data, or infrastructure.
Components:
1. System Components:
- Represents the internal components of the system, including software, hardware, and network infrastructure.
2. Third-Party Activities:
- Activities performed by external vendors on behalf of the system owner.
- Examples include software development, data processing, system maintenance, or cloud hosting.
Data Flows:
1. System Owner to Third-Party Vendors:
- Involves communication, coordination, and delegation of tasks or responsibilities to third-party vendors.
- May include sharing system documentation, access privileges, or specific project requirements.
2. Third-Party Vendors to System Components:
- Involves the execution of activities by third-party vendors on the system components.
- May include development, maintenance, or hosting of system components.
3. System Components to Third-Party Vendors:
- Involves the exchange of data, credentials, or system components between the system and third-party vendors.
- May include data processing, data storage, or system integration.
Interactions:
1. System Owners:
- Responsible for overseeing the system's operations, security, and compliance.
- Should establish clear expectations, requirements, and agreements with third-party vendors regarding oversight and monitoring.
2. Third-Party Vendors:
- Engaged to perform specific activities or provide services related to the system.
- Should adhere to the agreed-upon oversight and monitoring requirements and provide necessary information or reports as requested.
3. Trust Boundaries:
- Points where the system interacts with external entities, including third-party vendors.
- Should be identified and defined to clearly delineate the responsibilities and access privileges of third-party vendors.
4. Data Privacy:
- Focuses on protecting sensitive data from unauthorized access, use, or disclosure.
- System owners should ensure that third-party vendors handle sensitive data in compliance with data privacy regulations and industry standards.
5. Regulatory Compliance:
- Involves adhering to relevant laws, regulations, and industry standards.
- System owners should ensure that third-party vendors comply with applicable regulations and standards in their activities.
Threat detection
| Abnormal network traffic | Potential threats |
|---|---|
Port/host scan | The port or host scan behaviors mean one of the hosts may have been infected by a malware program, and the malware program is looking for vulnerabilities, other services, or hosts on the network. |
A high number of outbound DNS requests from the same host | This is a symptom of Command and Control (C&C) malware, establishing communication between the infected host and the C&C server using the DNS protocol. |
A high number of outbound HTTP requests from the same host | This is a symptom of C&C, establishing communication between the infected host and the C&C server using the HTTP protocol. |
Periodical outbound traffic with samesized requests or during the same period of time every day | This is a symptom of C&C malware, establishing communication between the infected host and the C&C server. |
Outbound traffic to an external web or DNS listed as a known threat by threat intelligence feeds | The user may be tricked through social engineering to connect to an external known threat web or the C&C connection is successfully established. |
To visualize the network threat status, there are two recommended open source tools: Malcom and Maltrail (Malicious Traffic detection system). Malcom can present a host communication relationship diagram. It helps us to understand whether there are any internal hosts connected to an external suspicious C&C server or known bad sites https://github.com/tomchop/malcom#what-is-malcom
Indicators of compromises
An analysis of hosts for suspicious behaviors also poses a significant challenge due to the availability of logs. For example, dynamic runtime information may not be logged in files and the original process used to drop a suspicious file may not be recorded. Therefore, it is always recommended to install a host IDS/IPS such as OSSEC (Open Source HIDS SEcurity) or host antivirus software as the first line of defense against malware. Once the host IDS/IPS or antivirus software is in place, threat intelligence and big data analysis are supplementary, helping us to understand the overall host’s security posture and any known Indicators of Compromises (IoCs) in existing host environments.
Based on the level of severity, the following are key behaviors that may indicate a compromised host:
External source client IP
The source of IP address analysis can help to identify the following: A known bad IP or TOR exit node Abnormal geolocation changes Concurrent connections from different geolocations The MaxMind GeoIP2 database can be used to translate the IP address to a geolocation: https://dev.maxmind.com/geoip/geoip2/geolite2/#Downloads
Client fingerprint (OS, browser, user agent, devices, and so on)
The client fingerprint can be used to identify whether there are any unusual client or non-browser connections. The open source ClientJS is a pure JavaScript that can be used to collect client fingerprint information. The JA3 provided by Salesforce uses SSL/TLS connection profiling to identify malicious clients. ClientJS: https://clientjs.org/ JA3: https://github.com/salesforce/ja3
Web site reputation
When there is an outbound connection to an external website, we may check the threat reputation of that target website. This can be done by means of the web application firewall, or web gateway security solutions https://www.virustotal.com/
Random Domain Name by Domain Generation Algorithms (DGAs)
The domain name of the C&C server can be generated by DGAs. The key characteristics of the DGA domain are high entropy, high consonant count, and long length of a domain name. Based on these indicators, we may analyze whether the domain name is generated by DGAs and could be a potential C&C server. DGA Detector: https://github.com/exp0se/dga_detector/ In addition, in order to reduce false positives, we may also use Alexa’s top one million sites as a website whitelist. Refer to https://s3.amazonaws.com/alexa-static/top-1m.csv.zip.
Suspicious file downloads
Cuckoo sandbox suspicious file analysis: https://cuckoosandbox.org/
DNS query
In the case of DNS query analysis, the following are the key indicators of compromises: DNS query to unauthorized DNS servers. Unmatched DNS replies can be an indicator of DNS spoofing. Clients connect to multiple DNS servers. A long DNS query, such as one in excess of 150 characters, which is an indicator of DNS tunneling. A domain name with high entropy. This is an indicator of DNS tunneling or a C&C server.
