Resources
Table of contents
- Resources
- Books
- Hands-On Security in DevOps
- Practical Threat Intelligence and Data-Driven Threat Hunting: A hands-on guide to threat hunting with the ATT&CK™ Framework and open source tools
- Operationalizing Threat Intelligence: A guide to developing and operationalizing cyber threat intelligence programs
- Web Application Security: Exploitation and Countermeasures for Modern Web Applications
- Practical Application Security
- Guidelines
- Framework
- Cheatsheet
- Lab
- Threats
- Books
Books
Hands-On Security in DevOps

Practical Threat Intelligence and Data-Driven Threat Hunting: A hands-on guide to threat hunting with the ATT&CK™ Framework and open source tools

Get to grips with cyber threat intelligence and data-driven threat hunting while exploring expert tips and techniques
Practical Threat Intelligence and Data-Driven Threat Hunting
Operationalizing Threat Intelligence: A guide to developing and operationalizing cyber threat intelligence programs

Learn cyber threat intelligence fundamentals to implement and operationalize an organizational intelligence program
Operationalizing Threat Intelligence
Web Application Security: Exploitation and Countermeasures for Modern Web Applications

While many resources for network and IT security are available, detailed knowledge regarding modern web application security has been lacking―until now. This practical guide provides both offensive and defensive security concepts that software engineers can easily learn and apply.
Web Application Security: Exploitation and Countermeasures for Modern Web Applications
Practical Application Security

A Book About more +15 Vulnerability Type Attack & Defence and Tutorial About Software Security Tools and Appliance.
Practical Application Security
Guidelines
OWASP DevSecOps Guidelines
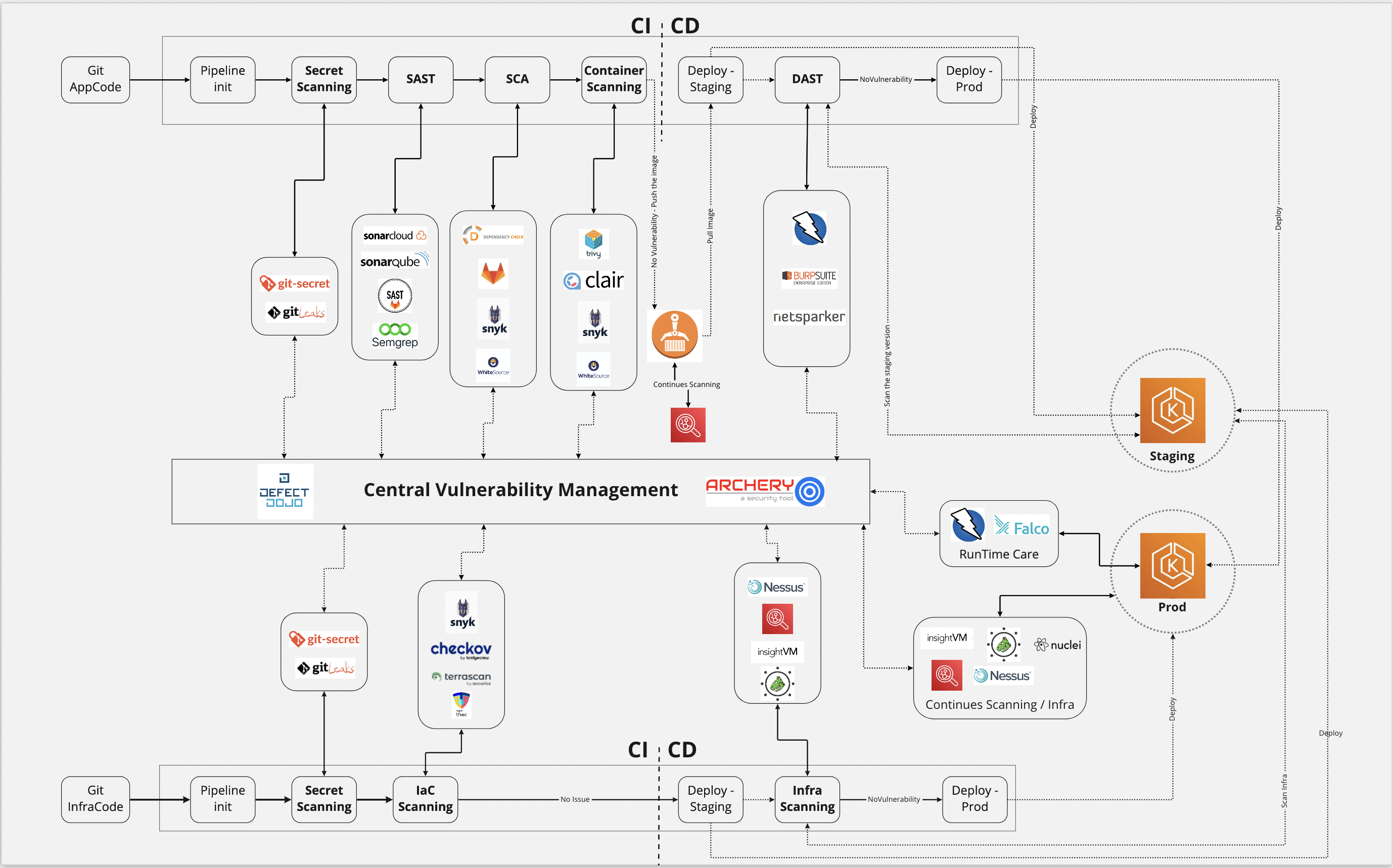
The OWASP DevSecOps Guideline explains how we can implement a secure pipeline and use best practices and introduce tools that we can use in this matter. Also, the project is trying to help us promote the shift-left security culture in our development process. This project helps any companies of each size that have a development pipeline or, in other words, have a DevOps pipeline. We try to draw a perspective of a secure DevOps pipeline during this project and then improve it based on our customized requirements.
6mile DevSecOps Playbook
This playbook will help you introduce effective DevSecOps practices in your company, regardless of size. We provide explicit guidance and actionable steps to introduce security controls, measure their effectiveness, and demonstrate value for money to your business leaders. Following this playbook will help teams build materially more secure applications, and that in the end, is the intent.
Aif4thah Dojo-101
Knowledge base in cybersecurity, administration and secure development
sottlmarek DevSecOps
AcalephStorage Awesome DevSecOps
AcalephStorage Awesome DevSecOps
wmariuss Awesome DevOps
zoidbergwill Awesome eBPF
Framework
Cloud Adoption Framework
Proven guidance and best practices that help you confidently adopt the cloud and achieve business outcomes.
Microsoft Cloud Adoption Framework
Cheatsheet
Hi! I’m Lars Windolf and my expertise is on system architecture and DevSecOps. I strongly care about collecting and sharing knowledge and use this site as a resource for my daily work.
Lab
Actionable Adversary Emulation for the Cloud
Proven guidance and best practices that help you confidently adopt the cloud and achieve business outcomes.
Granular, Actionable Adversary Emulation for the Cloud
AWS Threat Simulation and Detection
sbasu7241 AWS Threat Simulation and Detection
